ToC
开始
由于 <a> 设置了 pointer-events: none; 因此无法点击。复制链接进入第一题。
一只方熊猫
下载后发现图片无法打开:

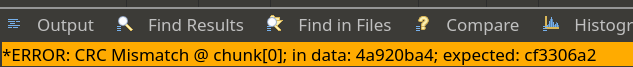
使用 010Editor 打开后提示 CRC 错误:
随便找了个爆破图片宽高的脚本:
# -*- coding: utf8 -*-
import osimport binasciiimport structmisc = open("panda.png","rb").read()
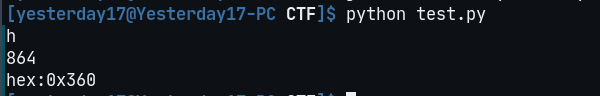
# 爆破宽for i in range(1024): data = misc[12:16] + struct.pack('>i',i)+ misc[20:29] #IHDR数据 crc32 = binascii.crc32(data) & 0xffffffff if crc32 == 0x4A920BA4: #IHDR块的crc32值 print("w") print(i) print("hex:"+hex(i))
# 爆破高for i in range(1024): data = misc[12:20] + struct.pack('>i',i)+ misc[24:29] crc32 = binascii.crc32(data) & 0xffffffff if crc32 == 0x4A920BA4: print("h") print(i) print("hex:"+hex(i))拿脚本跑一下,得到图片的真正 height:
修改原文件,得到 flag:

根据 UUID 进入下一题。
🤝
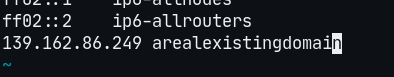
给出的链接是 http://arealexistingdomain/flag.html,第一想法就是在 /etc/hosts 里加个域名(
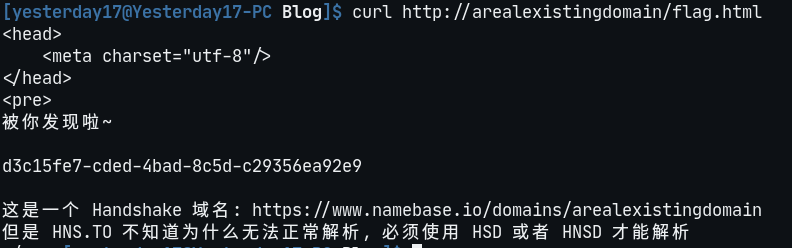
然后 curl 一下就出来了(
根据 UUID 进入下一题(
粗心的小明
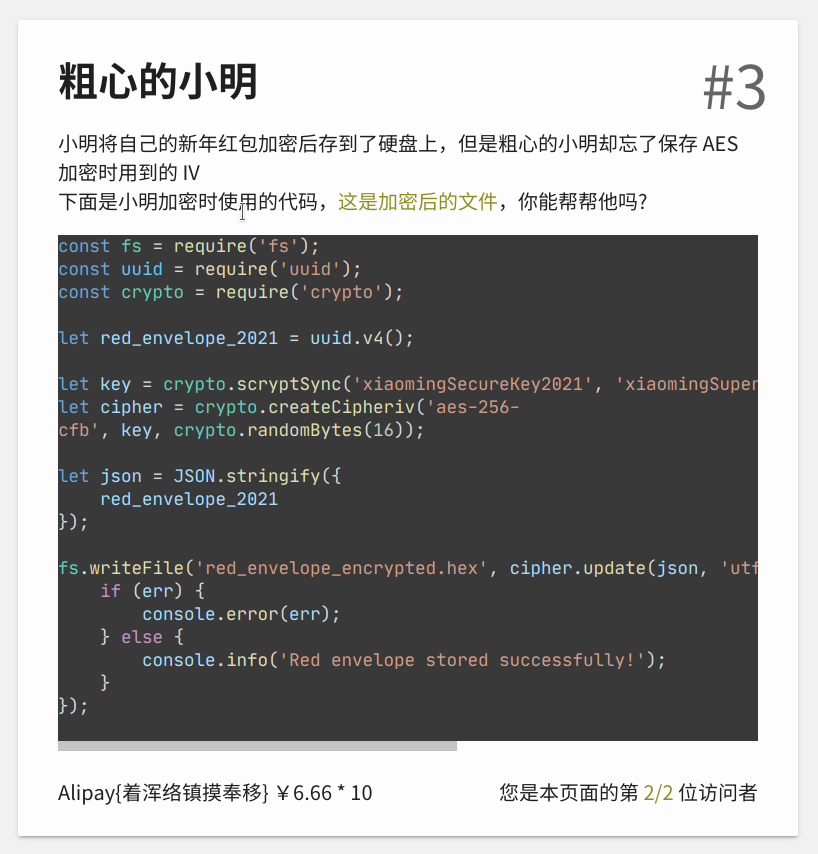
题中给出的代码如下:
const fs = require("fs");const uuid = require("uuid");const crypto = require("crypto");
let red_envelope_2021 = uuid.v4();
let key = crypto.scryptSync("xiaomingSecureKey2021", "xiaomingSuperSalt", 32);let cipher = crypto.createCipheriv("aes-256-cfb", key, crypto.randomBytes(16));
let json = JSON.stringify({ red_envelope_2021,});
fs.writeFile( "red_envelope_encrypted.hex", cipher.update(json, "utf8", "hex") + cipher.final("hex"), function (err) { if (err) { console.error(err); } else { console.info("Red envelope stored successfully!"); } });给出的 hex 如下:
d365895fbcdbd3a29b1bf00307429fd07d53ba3c0553b8789867d4aee3b8c3bbb0e5a8fd582a9696aabbdc1e373f97efac2529d588320800449553f6加密使用的是 aes-256-cfb,以 IV 作为初始文本,加密(encrypt_block)得到一个块(block_encrypted),再将 block_encrypted 和明文异或(⊕)得到密文(prev_ciphertext)。之后,再以 prev_ciphertext 为初始文本,加密得到下一个 block_encrypted,再与下一段明文异或……以此类推,如下图所示[1]:
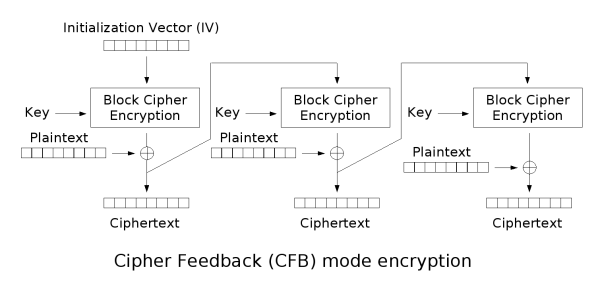
而文本的前半段是确定的,为 {"red_envelope_2021":,这已经超过了一个块的大小(16),因此可以通过第一个块得到 IV。简单步骤如下:
- 将原文转换为
hex:7b227265645f656e76656c6f70655f32 - 从密文中摘取第一块:
d365895fbcdbd3a29b1bf00307429fd0 - 异或得到
AES加密后的内容:a847fb3ad884b6cced7e9c6c7727c0e2 - 从
Node的运行结果中得到32位密钥:03da3479601ff722a6472329347a161bf8a712ead1d04b5560414be1dead3566 - 解密即可
解密使用了 boppreh/aes 的 AES 实现[2],修改后的脚本如下:
#!/usr/bin/env python3
s_box = ( 0x63, 0x7C, 0x77, 0x7B, 0xF2, 0x6B, 0x6F, 0xC5, 0x30, 0x01, 0x67, 0x2B, 0xFE, 0xD7, 0xAB, 0x76, 0xCA, 0x82, 0xC9, 0x7D, 0xFA, 0x59, 0x47, 0xF0, 0xAD, 0xD4, 0xA2, 0xAF, 0x9C, 0xA4, 0x72, 0xC0, 0xB7, 0xFD, 0x93, 0x26, 0x36, 0x3F, 0xF7, 0xCC, 0x34, 0xA5, 0xE5, 0xF1, 0x71, 0xD8, 0x31, 0x15, 0x04, 0xC7, 0x23, 0xC3, 0x18, 0x96, 0x05, 0x9A, 0x07, 0x12, 0x80, 0xE2, 0xEB, 0x27, 0xB2, 0x75, 0x09, 0x83, 0x2C, 0x1A, 0x1B, 0x6E, 0x5A, 0xA0, 0x52, 0x3B, 0xD6, 0xB3, 0x29, 0xE3, 0x2F, 0x84, 0x53, 0xD1, 0x00, 0xED, 0x20, 0xFC, 0xB1, 0x5B, 0x6A, 0xCB, 0xBE, 0x39, 0x4A, 0x4C, 0x58, 0xCF, 0xD0, 0xEF, 0xAA, 0xFB, 0x43, 0x4D, 0x33, 0x85, 0x45, 0xF9, 0x02, 0x7F, 0x50, 0x3C, 0x9F, 0xA8, 0x51, 0xA3, 0x40, 0x8F, 0x92, 0x9D, 0x38, 0xF5, 0xBC, 0xB6, 0xDA, 0x21, 0x10, 0xFF, 0xF3, 0xD2, 0xCD, 0x0C, 0x13, 0xEC, 0x5F, 0x97, 0x44, 0x17, 0xC4, 0xA7, 0x7E, 0x3D, 0x64, 0x5D, 0x19, 0x73, 0x60, 0x81, 0x4F, 0xDC, 0x22, 0x2A, 0x90, 0x88, 0x46, 0xEE, 0xB8, 0x14, 0xDE, 0x5E, 0x0B, 0xDB, 0xE0, 0x32, 0x3A, 0x0A, 0x49, 0x06, 0x24, 0x5C, 0xC2, 0xD3, 0xAC, 0x62, 0x91, 0x95, 0xE4, 0x79, 0xE7, 0xC8, 0x37, 0x6D, 0x8D, 0xD5, 0x4E, 0xA9, 0x6C, 0x56, 0xF4, 0xEA, 0x65, 0x7A, 0xAE, 0x08, 0xBA, 0x78, 0x25, 0x2E, 0x1C, 0xA6, 0xB4, 0xC6, 0xE8, 0xDD, 0x74, 0x1F, 0x4B, 0xBD, 0x8B, 0x8A, 0x70, 0x3E, 0xB5, 0x66, 0x48, 0x03, 0xF6, 0x0E, 0x61, 0x35, 0x57, 0xB9, 0x86, 0xC1, 0x1D, 0x9E, 0xE1, 0xF8, 0x98, 0x11, 0x69, 0xD9, 0x8E, 0x94, 0x9B, 0x1E, 0x87, 0xE9, 0xCE, 0x55, 0x28, 0xDF, 0x8C, 0xA1, 0x89, 0x0D, 0xBF, 0xE6, 0x42, 0x68, 0x41, 0x99, 0x2D, 0x0F, 0xB0, 0x54, 0xBB, 0x16,)
inv_s_box = ( 0x52, 0x09, 0x6A, 0xD5, 0x30, 0x36, 0xA5, 0x38, 0xBF, 0x40, 0xA3, 0x9E, 0x81, 0xF3, 0xD7, 0xFB, 0x7C, 0xE3, 0x39, 0x82, 0x9B, 0x2F, 0xFF, 0x87, 0x34, 0x8E, 0x43, 0x44, 0xC4, 0xDE, 0xE9, 0xCB, 0x54, 0x7B, 0x94, 0x32, 0xA6, 0xC2, 0x23, 0x3D, 0xEE, 0x4C, 0x95, 0x0B, 0x42, 0xFA, 0xC3, 0x4E, 0x08, 0x2E, 0xA1, 0x66, 0x28, 0xD9, 0x24, 0xB2, 0x76, 0x5B, 0xA2, 0x49, 0x6D, 0x8B, 0xD1, 0x25, 0x72, 0xF8, 0xF6, 0x64, 0x86, 0x68, 0x98, 0x16, 0xD4, 0xA4, 0x5C, 0xCC, 0x5D, 0x65, 0xB6, 0x92, 0x6C, 0x70, 0x48, 0x50, 0xFD, 0xED, 0xB9, 0xDA, 0x5E, 0x15, 0x46, 0x57, 0xA7, 0x8D, 0x9D, 0x84, 0x90, 0xD8, 0xAB, 0x00, 0x8C, 0xBC, 0xD3, 0x0A, 0xF7, 0xE4, 0x58, 0x05, 0xB8, 0xB3, 0x45, 0x06, 0xD0, 0x2C, 0x1E, 0x8F, 0xCA, 0x3F, 0x0F, 0x02, 0xC1, 0xAF, 0xBD, 0x03, 0x01, 0x13, 0x8A, 0x6B, 0x3A, 0x91, 0x11, 0x41, 0x4F, 0x67, 0xDC, 0xEA, 0x97, 0xF2, 0xCF, 0xCE, 0xF0, 0xB4, 0xE6, 0x73, 0x96, 0xAC, 0x74, 0x22, 0xE7, 0xAD, 0x35, 0x85, 0xE2, 0xF9, 0x37, 0xE8, 0x1C, 0x75, 0xDF, 0x6E, 0x47, 0xF1, 0x1A, 0x71, 0x1D, 0x29, 0xC5, 0x89, 0x6F, 0xB7, 0x62, 0x0E, 0xAA, 0x18, 0xBE, 0x1B, 0xFC, 0x56, 0x3E, 0x4B, 0xC6, 0xD2, 0x79, 0x20, 0x9A, 0xDB, 0xC0, 0xFE, 0x78, 0xCD, 0x5A, 0xF4, 0x1F, 0xDD, 0xA8, 0x33, 0x88, 0x07, 0xC7, 0x31, 0xB1, 0x12, 0x10, 0x59, 0x27, 0x80, 0xEC, 0x5F, 0x60, 0x51, 0x7F, 0xA9, 0x19, 0xB5, 0x4A, 0x0D, 0x2D, 0xE5, 0x7A, 0x9F, 0x93, 0xC9, 0x9C, 0xEF, 0xA0, 0xE0, 0x3B, 0x4D, 0xAE, 0x2A, 0xF5, 0xB0, 0xC8, 0xEB, 0xBB, 0x3C, 0x83, 0x53, 0x99, 0x61, 0x17, 0x2B, 0x04, 0x7E, 0xBA, 0x77, 0xD6, 0x26, 0xE1, 0x69, 0x14, 0x63, 0x55, 0x21, 0x0C, 0x7D,)
def sub_bytes(s): for i in range(4): for j in range(4): s[i][j] = s_box[s[i][j]]
def inv_sub_bytes(s): for i in range(4): for j in range(4): s[i][j] = inv_s_box[s[i][j]]
def shift_rows(s): s[0][1], s[1][1], s[2][1], s[3][1] = s[1][1], s[2][1], s[3][1], s[0][1] s[0][2], s[1][2], s[2][2], s[3][2] = s[2][2], s[3][2], s[0][2], s[1][2] s[0][3], s[1][3], s[2][3], s[3][3] = s[3][3], s[0][3], s[1][3], s[2][3]
def inv_shift_rows(s): s[0][1], s[1][1], s[2][1], s[3][1] = s[3][1], s[0][1], s[1][1], s[2][1] s[0][2], s[1][2], s[2][2], s[3][2] = s[2][2], s[3][2], s[0][2], s[1][2] s[0][3], s[1][3], s[2][3], s[3][3] = s[1][3], s[2][3], s[3][3], s[0][3]
def add_round_key(s, k): for i in range(4): for j in range(4): s[i][j] ^= k[i][j]
# learned from http://cs.ucsb.edu/~koc/cs178/projects/JT/aes.cxtime = lambda a: (((a << 1) ^ 0x1B) & 0xFF) if (a & 0x80) else (a << 1)
def mix_single_column(a): # see Sec 4.1.2 in The Design of Rijndael t = a[0] ^ a[1] ^ a[2] ^ a[3] u = a[0] a[0] ^= t ^ xtime(a[0] ^ a[1]) a[1] ^= t ^ xtime(a[1] ^ a[2]) a[2] ^= t ^ xtime(a[2] ^ a[3]) a[3] ^= t ^ xtime(a[3] ^ u)
def mix_columns(s): for i in range(4): mix_single_column(s[i])
def inv_mix_columns(s): # see Sec 4.1.3 in The Design of Rijndael for i in range(4): u = xtime(xtime(s[i][0] ^ s[i][2])) v = xtime(xtime(s[i][1] ^ s[i][3])) s[i][0] ^= u s[i][1] ^= v s[i][2] ^= u s[i][3] ^= v
mix_columns(s)
r_con = ( 0x00, 0x01, 0x02, 0x04, 0x08, 0x10, 0x20, 0x40, 0x80, 0x1B, 0x36, 0x6C, 0xD8, 0xAB, 0x4D, 0x9A, 0x2F, 0x5E, 0xBC, 0x63, 0xC6, 0x97, 0x35, 0x6A, 0xD4, 0xB3, 0x7D, 0xFA, 0xEF, 0xC5, 0x91, 0x39,)
def bytes2matrix(text): """ Converts a 16-byte array into a 4x4 matrix. """ return [list(text[i:i+4]) for i in range(0, len(text), 4)]
def matrix2bytes(matrix): """ Converts a 4x4 matrix into a 16-byte array. """ return bytes(sum(matrix, []))
def xor_bytes(a, b): """ Returns a new byte array with the elements xor'ed. """ return bytes(i^j for i, j in zip(a, b))
def inc_bytes(a): """ Returns a new byte array with the value increment by 1 """ out = list(a) for i in reversed(range(len(out))): if out[i] == 0xFF: out[i] = 0 else: out[i] += 1 break return bytes(out)
def pad(plaintext): """ Pads the given plaintext with PKCS#7 padding to a multiple of 16 bytes. Note that if the plaintext size is a multiple of 16, a whole block will be added. """ padding_len = 16 - (len(plaintext) % 16) padding = bytes([padding_len] * padding_len) return plaintext + padding
def unpad(plaintext): """ Removes a PKCS#7 padding, returning the unpadded text and ensuring the padding was correct. """ padding_len = plaintext[-1] assert padding_len > 0 message, padding = plaintext[:-padding_len], plaintext[-padding_len:] assert all(p == padding_len for p in padding) return message
def split_blocks(message, block_size=16, require_padding=True): assert len(message) % block_size == 0 or not require_padding return [message[i:i+16] for i in range(0, len(message), block_size)]
class AES: rounds_by_key_size = {16: 10, 24: 12, 32: 14} def __init__(self, master_key): """ Initializes the object with a given key. """ assert len(master_key) in AES.rounds_by_key_size self.n_rounds = AES.rounds_by_key_size[len(master_key)] self._key_matrices = self._expand_key(master_key)
def _expand_key(self, master_key): """ Expands and returns a list of key matrices for the given master_key. """ # Initialize round keys with raw key material. key_columns = bytes2matrix(master_key) iteration_size = len(master_key) // 4
# Each iteration has exactly as many columns as the key material. columns_per_iteration = len(key_columns) i = 1 while len(key_columns) < (self.n_rounds + 1) * 4: # Copy previous word. word = list(key_columns[-1])
# Perform schedule_core once every "row". if len(key_columns) % iteration_size == 0: # Circular shift. word.append(word.pop(0)) # Map to S-BOX. word = [s_box[b] for b in word] # XOR with first byte of R-CON, since the others bytes of R-CON are 0. word[0] ^= r_con[i] i += 1 elif len(master_key) == 32 and len(key_columns) % iteration_size == 4: # Run word through S-box in the fourth iteration when using a # 256-bit key. word = [s_box[b] for b in word]
# XOR with equivalent word from previous iteration. word = xor_bytes(word, key_columns[-iteration_size]) key_columns.append(word)
# Group key words in 4x4 byte matrices. return [key_columns[4*i : 4*(i+1)] for i in range(len(key_columns) // 4)]
def encrypt_block(self, plaintext): """ Encrypts a single block of 16 byte long plaintext. """ assert len(plaintext) == 16
plain_state = bytes2matrix(plaintext)
add_round_key(plain_state, self._key_matrices[0])
for i in range(1, self.n_rounds): sub_bytes(plain_state) shift_rows(plain_state) mix_columns(plain_state) add_round_key(plain_state, self._key_matrices[i])
sub_bytes(plain_state) shift_rows(plain_state) add_round_key(plain_state, self._key_matrices[-1])
return matrix2bytes(plain_state)
def decrypt_block(self, ciphertext): """ Decrypts a single block of 16 byte long ciphertext. """ assert len(ciphertext) == 16
cipher_state = bytes2matrix(ciphertext)
add_round_key(cipher_state, self._key_matrices[-1]) inv_shift_rows(cipher_state) inv_sub_bytes(cipher_state)
for i in range(self.n_rounds - 1, 0, -1): add_round_key(cipher_state, self._key_matrices[i]) inv_mix_columns(cipher_state) inv_shift_rows(cipher_state) inv_sub_bytes(cipher_state)
add_round_key(cipher_state, self._key_matrices[0])
return matrix2bytes(cipher_state)
if __name__ == '__main__': from base64 import b64encode from binascii import unhexlify ret=AES(unhexlify('03da3479601ff722a6472329347a161bf8a712ead1d04b5560414be1dead3566')).decrypt_block(unhexlify('a847fb3ad884b6cced7e9c6c7727c0e2')) print(b64encode(ret))得到 IV 的 base64:Jle9TPezMnv770Y5b+Wc1g==,最后使用 CyberChef 解密:
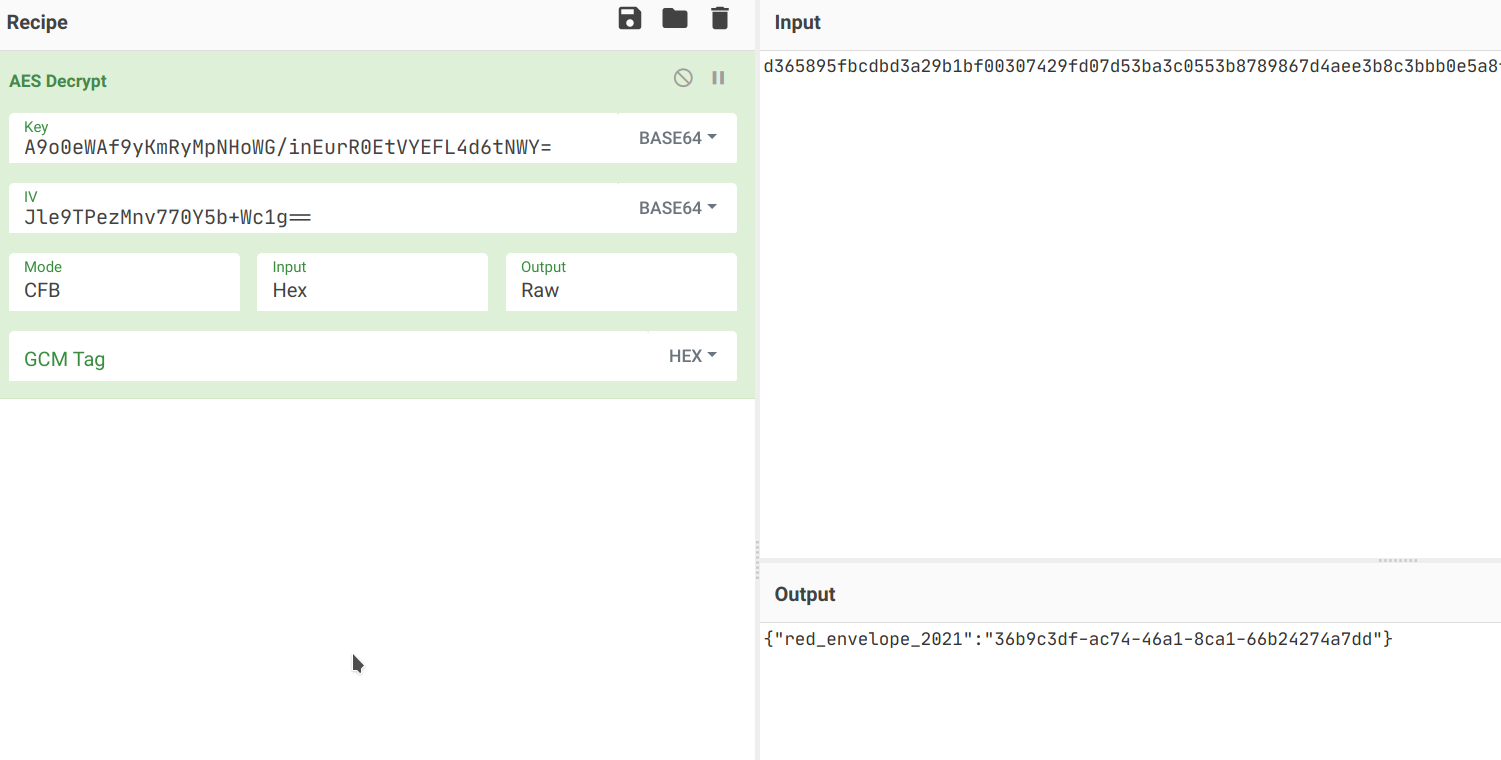
得到下一题的地址。
太 🆒 啦
找了好久,结果 Esolang Wiki 还真有全名就叫这个的语言[3](
题面如下:
🆕6️⃣🍿🍔🌭🥪🌮🍆🥑💬🍔💬🌭💬🥪💬🌮💬🍆💬🥑🛑🆕🔟🤔🖇🙃🍖🍟🥔🌽🥩🥕🌶️🌯🥥❓🆓⚖️🆓✖️🆓➗🙃🔢1️⃣8️⃣4️⃣7️⃣🔢🛑4️⃣🛑🔢2️⃣4️⃣8️⃣🔢🛑🆓🍿🌶️🥥🌽🥕🌽🥔🍿🌽🍖🌽🥩🌯🍟🛑🆓💬🔤🚫📥️🔛🔤🛑🛑💬🔤💻🔑🔑🔑🔑🔑🔑🔤🤔🎛️🔤9️⃣❤️9️⃣4️⃣🔤🔤1️⃣9️⃣7️⃣4️⃣🔤🔤4️⃣💜💛7️⃣🔤🔤➖🔤🔤🧡7️⃣9️⃣9️⃣🔤🔤8️⃣❤️4️⃣💛🔤🔤💚6️⃣0️⃣💛🔤🔤2️⃣5️⃣💙1️⃣🔤🔤2️⃣3️⃣7️⃣2️⃣🔤提示
做
❤️ A 🧡 B 💛 C 💚 D 💙 E 💜 F于是下面分析的内容就将这些红心全都替换成对应的文本了。
🍿
按 square-cool 仓库[4] 的描述,🆕 是定义函数,后面跟随一个数字 n,表示参数的数量,然后是函数名 emoji,最后的 n 个 emoji 表示参数名,函数以 🛑 结尾。于是开头的一一部分可以翻译成下面的形式:
# 🍿: Print six arguments🆕6️🍿
🍔🌭🥪🌮🍆🥑
💬🍔💬🌭💬🥪💬🌮💬🍆💬🥑
🛑其中 💬 是内置的函数,表示输出。这个函数的功能也就是连续输出对应的 6 个参数。
🤔
同样是一个函数,翻译如下:
# 🤔:🆕🔟🤔🖇 # modifier🙃 # input🍖 # p1🍟 # p2🥔 # p3🌽 # p4🥩 # p5🥕 # p6🌶️ # p7🌯 # p8🥥 # p9❓ # Returns the second argument if the first is true, otherwise returns the third argument.# input / 1847 * 4 == 2️4️8️🆓 ⚖️ 🆓 ✖️ 🆓 ➗🙃🔢1️8️4️7️🔢 🛑 4️ 🛑 🔢2️4️8️🔢🛑
🆓 # 🍿(p7, p9, -, p6, -, p3) 🍿🌶️🥥🌽🥕🌽🥔 # 🍿(-, p1, -, p5, p8, p2) 🍿🌽🍖🌽🥩🌯🍟🛑
🆓 # print('🚫📥️🔛') 💬🔤🚫📥️🔛🔤🛑
🛑其中 🆓 的功能类似作用域开始,并以 🛑 结束。
最后
# main# print('💻🔑🔑🔑🔑🔑🔑')💬🔤💻🔑🔑🔑🔑🔑🔑🔤
# 🤔(stdin, '9️A9️4️', '1️9️7️4️', '4️FC7️', '-', 'B7️9️9️', '8️A4️C', 'D6️0️C', '2️5️E1️', '2️3️7️2️')# d60c2372-8a4c-4fc7-9a94-b79925e11974🤔🎛️🔤9️A9️4️🔤🔤1️9️7️4️🔤🔤4️FC7️🔤🔤➖🔤🔤B7️9️9️🔤🔤8️A4️C🔤🔤D6️0️C🔤🔤2️5️E1️🔤🔤2️3️7️2️🔤最后就是调用了,其中 🎛️ 表示从 stdin 读入一个整数,但在实际分析中并没有起到作用。
最后得到 UUID:d60c2372-8a4c-4fc7-9a94-b79925e11974,进入终章。
Happy 2021
游戏结束,新年快乐!あけましておめでとうございます!(笑)